The Backup and Restore File Tree dialog contains information about:
Domain or LAN network and local drives
Local drives
Folders
Files
The Target dialog is separate from the Backup and Restore Trees. The Target is shown in a pop-up dialog window with the same type of information as listed above, without the right-mouse features.
When creating a Backup session the File Tree pane is where you select and/or cancel the selection of drives, folders and files that will be used as the Source.
When creating a Restore session the File Tree dialog is where you select and/or cancel the selection of drives, folders and files that will be used as the Target.
![]()
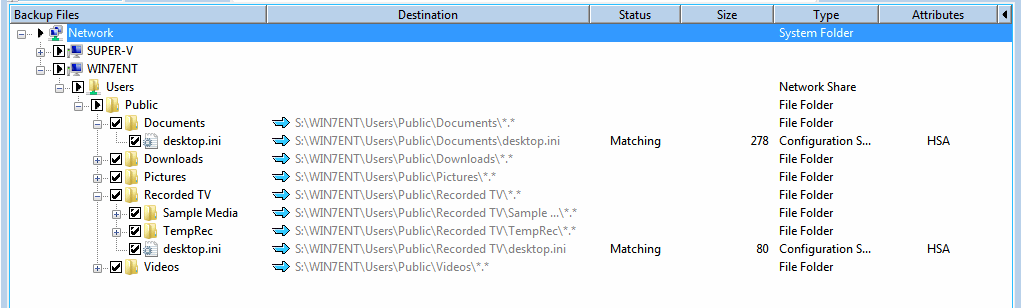
Source drives, folders and files are shown to the left of the blue arrows. Target folders and files are shown to the right of the blue arrows.
In the 'Restore Files' pane and under the 'Source' column the drive, folders and files are shown to the right of the![]() arrows that will be restored during a restore process.
arrows that will be restored during a restore process.
Notice the 'Backup Files' pane and under the 'Destination' column. The files to the right of the ![]() arrows are the files that are copied to the Target during a backup session.
arrows are the files that are copied to the Target during a backup session.
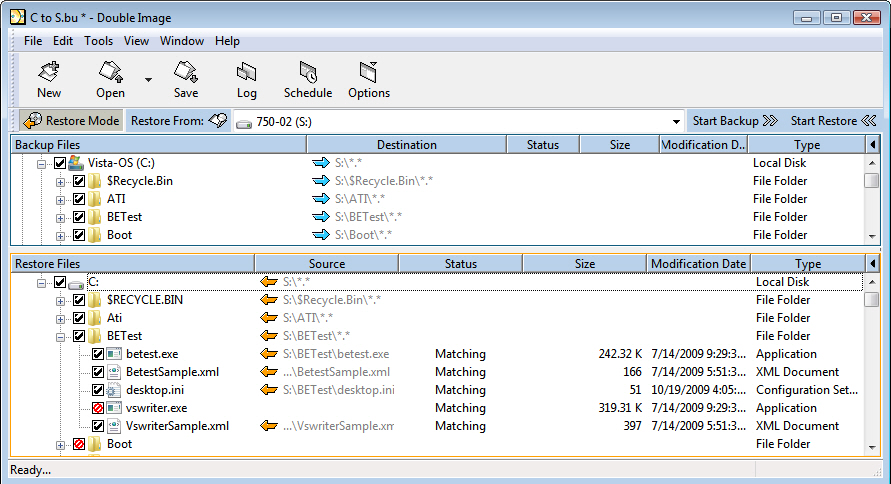
We created a backup profile and saved it as 'C to S.bu'.
Only the C: drive was selected for backup. It has the only complete check mark. A broken check mark indicates a child folder or file.
An actual backup occurred prior to viewing the above example. C: drive was copied to S: drive (accept for Omitted Paths). We know a backup was run because you can see 'matching' in the 'Status' column of the Restore Files list; and the Restore Files list can be expanded. If a backup was not done, then the Restore Files list could not be expanded like it is here. To carry this further, we could click menu->Tools->History... and see a history of all backup and restore sessions for this profile.
We know that the backup file name convention was relative only because parent folder names do not precede each source drive or folder or file on the target S:. How do we know that? Well, you can look under the Destination column of Backup Files (blue). The blue arrow points to the Target and what the copied source will look like following a backup process.
Both Backup Files and Restore Files are shown. We are able to see both trees by pressing {Ctrl} B keys at the same time, or from the View menu, 'Show Both Backup and Restore Files'. When {Ctrl} B is pressed again, the pane will show only the Backup Files or the Restore Files, depending on which was hi-lighted at the time. Try it next time you create a profile. Usually you won't show both trees at the same time until it's time to restore something, but for 'show and tell' both are shown.
Let's assume that we need to restore to C: from our original target drive S: and we don't want to restore all of the original backed up files. In the Restore Files shown above we double-click and expand the 'BETest' folder, then see its files. We do not want to restore 'vswriter.exe' file so we de-select ![]() it. Also, the folder 'Boot' will not be restored because it is also de-selected.
it. Also, the folder 'Boot' will not be restored because it is also de-selected.
'$Recycle.Bin' will not be restored, even though it shows that it has inherited a check mark from its parent C:.
With both backup and restore, the 'Omitted Paths' prevent certain system folders and files from being backed up and restored. See menu->Edit->Preferences->Omitted Paths. Omitted Paths contains '$Recycle.Bin' for one of its filtered paths.
Note, if we just create a profile and do not use it in an actual backup session then you would not be able to see the expanded Restore tree -- why show you something that does not yet exist?
The File Tree is normally shown with the options panel sharing the left side of the screen and the File Tree to the right. The options panel may be closed using the "X" icon on the options panel. The options panel may be opened or closed by clicking the Details Icon, or through the View menu, clicking Hide/Show Details.
The Files column displays a tree of drives, folders, sub-folders and files.
In Backup Mode, "Destination" defines the drives, folders and files where the files are to be copied to.
The terms 'Destination' and 'Target' have the same meaning.
The size of the folder or file in kilobytes.
The status column show the status of the folder or file. After a copy process is complete, the Trees are refreshed and the 'Status column' is present with the following values:
|
Status Column |
Description |
|
Matching |
Matching |
|
Updating |
File is being updated |
|
Sizes Differ |
File sizes are different |
|
No File |
No file information can be found for the file or folder in backup or restore tree. Usually indicates an I/O error. |
|
Backup Tree Only |
|
|
Newer |
The Source is newer than the Target file |
|
Older |
The Source is older than the Target file |
|
No Target |
No source file corresponds to this file |
|
Restore Tree Only |
|
|
Newer |
The Restore file is newer than the Target file |
|
Older |
The Restore file is older than the Target file |
|
No Source |
No source file corresponds to this file |
|
No Target |
The file exists on the Source but not on the Target. |
The date the file was last modified by a program. This is the same date that Windows Explorer provides.
File attributes defined by the Windows operating system and disk file system are described below.
Note, that much of the following reading may not be that much fun to try and understand on day one. This detail is included largely to help system administrators and those with a more technical interest to understand how Double Image handles copying files, based on Attributes. Some of the Attributes are new since the arrival of Windows Vista, Windows 7 and Windows 2008 Servers.
|
Code |
Value |
Meaning |
|
A |
ARCHIVE |
A file or directory that is an archive file or directory. Any time a file or directory is written, the Archive attribute is set (turned on ). Most backup programs will depend on this attribute to determine if files are to be backed up. Note, the default method used by Double Image is Incremental by Timestamp; however the use of the Archive attribute can also be relied on, should the user deem it necessary. One reason for not selecting the use of the Archive attribute in the Double Image selections is to permit other backup software to back up the same files that Double Image does, without collision problems related to set and not set of the Archive attribute. |
|
H |
HIDDEN |
The file or directory is hidden. It is not included in default views of directory listings in Windows Explorer, unless folder options are set to view Hidden and System files. Double Image will show these files, regardless. Double Image provides an option for copying hidden files. The hidden files attribute can be changed by the user, but changing the attribute is not recommended because hidden files often relate to environmental operation and the operating system and should not normally be removed or modified. |
|
I |
INDEXED |
[Windows NTFS only] - Folders and files are indexed by the Windows Indexing Service on Windows NTFS drives when using this attribute. Once files are indexed, users can use queries to search in files in different formats and languages. See Windows HELP for details using Windows Indexing Service. FILE_ATTRIBUTE_NOT_CONTENT_INDEXED - The file or directory is not to be indexed by the Windows content indexing service. see Properties, Advanced for a Folder or File. |
|
O |
OFFLINE |
The data of a Offline file is not available immediately. This attribute indicates that the file data is physically moved to offline storage. This attribute is used by Remote Storage, which is the hierarchical storage management software. Applications should not arbitrarily change this attribute, however Double Image can backup Offline files, if the option is selected. |
|
R |
READONLY |
With the Read-Only attribute set, folders and files cannot be modified by writing to them or deleting them. This attribute is often used by the environmental software, operating system, and some applications requiring files to remain safe from accidental change. Double Image provides an option for copying Read-only files. Double Image will copy Read Only files just fine and following a copied file the Read-Only attribute is the same on the target file as the source file. |
|
S |
SYSTEM |
A file or directory that the operating system uses a part of, or uses exclusively. These file are normally not shown in the Windows Explorer view, unless the folder options are selected to show them. Double Image can copy system files and will always show these files in its folder-file tree view.. |
|
T |
TEMPORARY |
The file is temporary. File systems attempt to keep all of the data in memory for quicker access rather than flushing the data back to mass storage. A temporary file is normally deleted by the application as soon as it is no longer needed. |
|
C |
COMPRESSED |
The file is compressed. On a Windows NTFS file system volume, each file and directory has a compression attribute. Other file systems may also implement a compression attribute for individual files and directories. If a file's compression attribute is set (COMPRESSED) all data in the file is compressed. If the attribute is clear, none of the data in the file is compressed. There is no partially compressed state. The compression algorithm used is that of Windows, therefore with regard to Double Image, if a file is compressed we can say Windows compression is used. To be more technical the file compression algorithm used by the NTFS file system is 'Lempel-Ziv' compression. This is a lossless compression algorithm which means that no data is lost when compressing and decompressing the file as opposed to lossy compression algorithms such as JPEG where some data could be lost each time data compression and decompression occurs. Directories or files can be compressed or encrypted but not both compressed and encrypted. |
|
D |
DIRECTORY |
Defines the object as a directory (also called 'folder'). |
|
E |
ENCRYPTED |
Windows NTFS only. Directories and files can be encrypted on Windows NTFS volumes. The directories or files can be compressed or encrypted but both not compressed and encrypted. Microsoft Windows provide a feature named Windows Encrypting File System (EFS). This feature provides the ability to encrypt files and directories on volumes that have been previously formatted or converted to the Windows NTFS file system (not to confuse this with Linux NTFS file system -- they are different in this regard). Unlike files, the contents and streams of directories are not encrypted. Instead, when a directory is encrypted, files placed within the directory are automatically encrypted. When viewing the properties of a file, only an administrator or user with administrator privileges can decrypt encrypted files or encrypt decrypted files. A global key is associated with the administrator account, meaning that administrator security privileges are always required when changing file encryption or decryption attributes.When files are encrypted it is the Windows operating system that provides the Encrypting File System (EFS) used by Double Image during backup and restore sessions. Double Image will copy either compressed or encrypted files, however if the target file is encrypted, and if a file on the source is compressed the target file will remain encrypted. If a file is encrypted on the source and not on the target the source file will be copied and encrypted to the target. An example of good use for local computer data encryption is to be able to create off-site storage on another computer, and only you have the keys to the data. Windows EFS CertificateThe security is represented by EFS certificates and keys that only the creator user has access to. Certificates are a digital document that verifies the identity of a person or indicates the security of a computer, file or web site. Certificates are issued by trusted companies known as Certification Authorities (CA).Since Windows encrypted files (used by Double Image) are tied to a certificate for the logged on user creating the encrypted files, copying files to another computer will not render them available for use on the other computer, unless the certificates of the creating user are imported to that other computer. Take a case where user Joe copies his encrypted files from \\JoesMachine\Joe\ to another computer user \\SallysMachine\Sally\. The files cannot be used by anyone other than Joe on the machine from which the backup task was run. Double Image can backup and restore these files just fine, provided Double Image runs with 'Joes' user credentials and where Joe has his EFS certificated keys. Under another situation, let's say you backup your encrypted data to a removable hard drive, then at some later date need to also use that same hard drive on a new operating system or on another computer. What do you do? Well, you find the flash drive or floppy where you exported your certificates to or logon to the computer that created the encrypted files and export your certificates to a flash drive or floppy -- then import the certificates to the new computer or operating system; And you will be able to access the encrypted files. With this tidbit of information, if you have encrypted files on your machine, do you have a backup of your certificates that only Windows will let you get to? It is very important to back up your Windows EFS certificate keys to a separate disk, like a flash drive or floppy or CD. Do this before the day comes when you will need them. What if your machine crashes and cannot be brought back to operation and you did not backup your certificate keys for your encrypted files? --big headache; no one can recover those files for you without your EFS certificate keys, not even Double Image. To export and backup your certificates, start by searching for "certificates' in Windows Start search or Help provided by the operating system you use. |
|
L |
REPARSE_POINT |
The REPARSE_POINT attribute has what are called tags to further define the type of folder or file. You won't see these tags, but Double Image does. The tags define what are technically called 'hard links',' junctions', and 'symbolic links'. They also include 'mount points'. Shortcuts have basic link-to-file relationship. A shortcut is very small file, usually with the .lnk extension. Shortcuts can be copied, renamed, or deleted; file operations on a shortcut don't affect the object being pointed to. Even though, shortcuts are a type of Windows symbolic link you can still delete and rename shortcuts without deleting or renaming its reference. Symbolic Links will appear in the user interface as a folder, but in reality they are a file-system object that points to another file system object in a different physical location. These links appear as normal files or directories, and can be acted upon by the user or application in exactly the same manner. Symbolic links are designed to aid in migration and application compatibility. This is new stuff on Windows Vista machines and higher and was first developed on UNIX operating systems. It is our opinion that in a backup and recovery operation copying certain links could eventually open the door for data loss problems. For example, those running a Windows 7 operating system may have seen the folder 'All Users', a <symbolic link>. 'All Users' really points to 'C:\Program Data' folder contents. If the symbolic link 'C:\users\all users' was copied to 'F:\users\all users' then both links point to the same 'C:\Program Data folder'. Evidently, Windows keeps a count of multiple symbolic links for a given reference (target); but should that count not be 100% accurate for some reason and one day you decide to delete 'F:\users\all users' to get some needed disk space, might it be possible to delete the entire 'C:\Program Data' folder'? 'C:\Program Data' folder is very important for your operating systems environment to keep functioning. |
|
P |
SPARSE_FILE |
Sparse files are typically large files whose data are mostly zeros. This is a mild form of compression, where the large groups of repeated data are delimited to reduce the size of the file on writing. On reading the data is expanded for the application using the file. |
Columns can be re-positioned by using the mouse to drag left or right of other columns.
Remove viewing of a column by using the mouse to drag the column off the column bar.
Reapply viewing of a column by right clicking the column bar and check or clear desired columns; OR click the change column arrow located on the far right column bar to check or clear desired columns.
Destination
Status
Modification Date
Type
Size
Attributes
Source
Status
Size
Modification Date
Type
Attributes
A drive can be a local, external or network drive. External drives can be
IDE
SCSI
USB
Firewire
Memory Sticks (usually connected via USB ports)
Network drives may be mapped to a drive letter or referenced using UNC (using computer name).
A folder can represent sub-folders or files.
Double-click a drive or folder name to see the folder expand or collapse. Single-click a folder or file box to:
check (select) a drive, folder or file for backup or restore
uncheck (clear) a drive, folder or file for backup or restore
cancel individual folders and files amongst other selected folders and files
expand
check <toggle> uncheck
insert folder
insert file
view properties
The check-boxes shown above on the left have a hierarchy over those on the right. Checking ![]() a drive or parent folder causes all sub-folders and files to become a child
a drive or parent folder causes all sub-folders and files to become a child ![]() by default. You can de-select
by default. You can de-select ![]() sub-folders and files you choose not to backup.
sub-folders and files you choose not to backup.
The arrow symbols show the precise Target for the selected folder or file. When selecting folders only, each Target path will end in '*.*' indicating all files within the selected folder have been chosen. If you select only a filename then the Target will show the Target path including the exact filename. During a backup session the arrow will show as ![]() . During a restore session the arrow will show as
. During a restore session the arrow will show as![]() .
.
Use File Save or File Save As to save the current profile. If you not Save the profile, a prompt will be displayed before a Backup or Restore session begins. A File Open can be used to make changes to the same profile. All the folder and file selections are retained in each profile for later use.
within Double Image itself
the Scheduler
a Desk Top icon
another application
a command line
by clicking a profile name when using Windows Explorer.
Filtering is the method of defining certain groups of files to be either copied or not copied. The Include and Exclude and Date-Time ranges can be used for this purpose.
Filtering can be applied in both Backup Mode and Restore Mode. Filtering is an user option and can be defined by the user to Include-Exclude file groups. File group filtering can also be done with Date-Time Ranges.