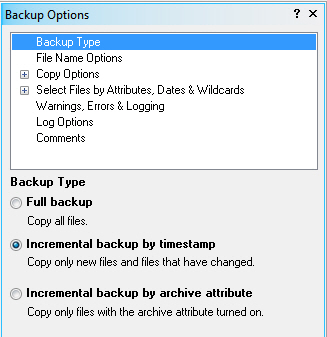

Full backup copies all files without depending file timestamp & size or file Archive bit.
The full backup option produces a complete backup of all files from source to target, regardless if files match or not. Normally setting is not used. A case where you may want to do a Full backup is when you would like to have a 'Verify' done on the entire source vs. target, in which case you would also turn on the Verify option. Otherwise, Incremental backup by timestamp is the most beneficial in terms of speed.
Using the file timestamp for incremental backups is very useful because the backups occur quickly. Only new files and files whose date, time or size has changed are copied. This method does not rely on the archive bit.
One benefit for using this option is that other backup systems can effectively and backup the same files done by Double Image; and again the reason is that this option ignores using of the archive bit.
Copies only files with a set (turned on) archive bit set. Files with a reset (cleared, turned off) archive bit are not be copied. This type of backup does not depend on a file's date, time, or size. Note, the file archive bit is set (turned on) when the file is added or modified in some way, regardless of the program that does the writing, including the operating system directly.
In addition to this option, users will usually need to have the archive bit reset for copied files. Older and traditional backup utilities usually rely on the file archive bit and therefore the archive bit is normally reset (turned off) after it is backed up. To accomplish the reset in Double Image use the Options panel, Select Files by Attributes, Dates & Wild cards, then check the box next to reset archive bit on copied source.
If for some reason you need to use this method of backup then a Full backup is normally done first making sure that all files will be copied to the target. (At some point, another backup program may have reset (turned off) the archive bit on some or all of the source files).
Different file systems store file time stamps differently (the modification date and time of a file).
NTFS is a standard Windows file system with time stamps kept in 100-nanosecond increments or ticks.
FAT and FAT32 is commonly used for older Windows 95, Windows 98 and Windows ME, including MS-DOS releases.
If the source and target drives are controlled by Windows then using Double Image's 'Incremental by timestamp' will deal with the different time stamp methods between NTFS, FAT and FAT32 and the more recent file system exFAT.
If the file system is not a Windows controlled device then Double Image make its best attempt to accommodate the different systems. Double Image can function with over 75 different file systems, including file systems for UNIX, Linux, HP, Samba, and many more which include most NAS and SAN devices. If you do not see your system included in this file system list, it is likely that it may still be acceptable to use 'Incremental by timestamp' backups.
If you believe that your NAS device is not properly supported let us know and we will include it in the next release of Double Image 7.
Most of the non-Windows controlled devices use a NTFS file system; however Windows NTFS and Linux file systems do not carry the exact file attributes, file permissions and file flags, as you might expect.
When using Double Image's native file copying, it may not be a good idea to rely on non-Windows controlled devices for backing up a Windows system drive or Windows EFS encrypted files on any drive; the non-Windows devices will not accept the exact file attributes from the Windows NTFS file system source files, including file security setting. On the other hand, if you need to backup data files then using non-Windows controlled devices should be fine. Hence, that is why most off-the-shelf NAS devices will use marketing terms similar to "..backup your music, pictures and data...". Let's say you copy your Windows system drive to a NAS Linux device; Double Image will create a log entry of the types of file attributes that will not be carried to the target. Also, log warning entries are created during the backup session of those files that cannot be copied exactly as the source is.